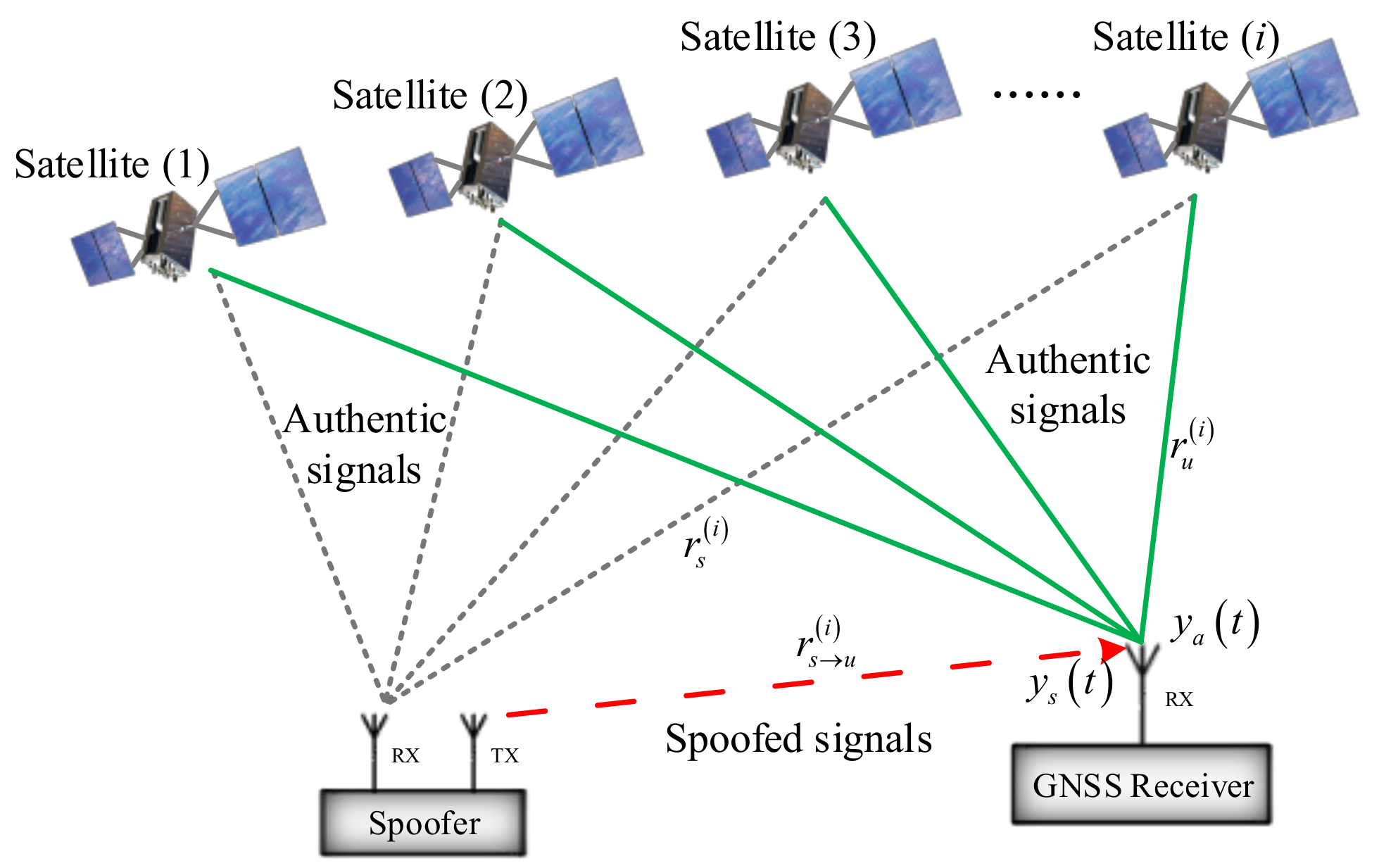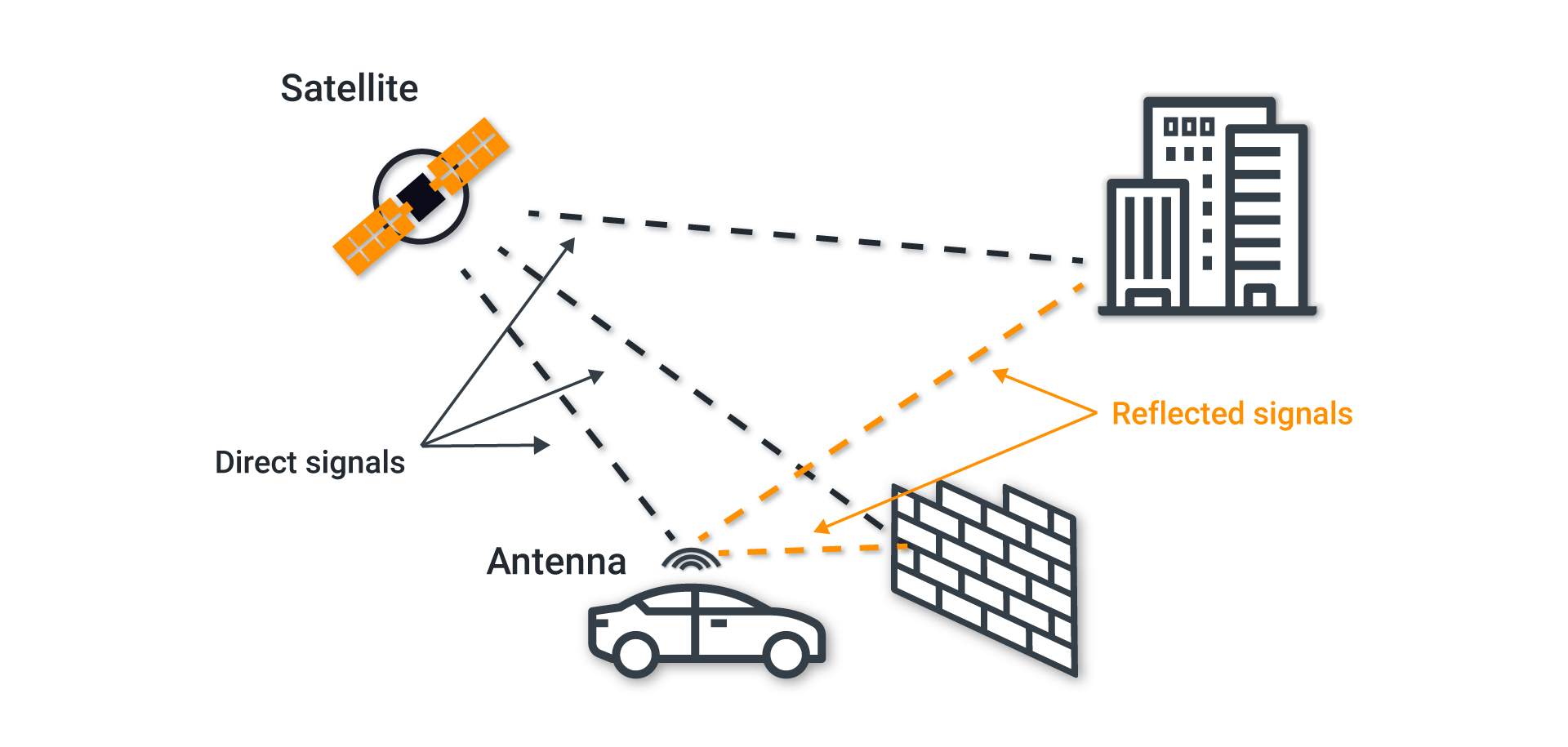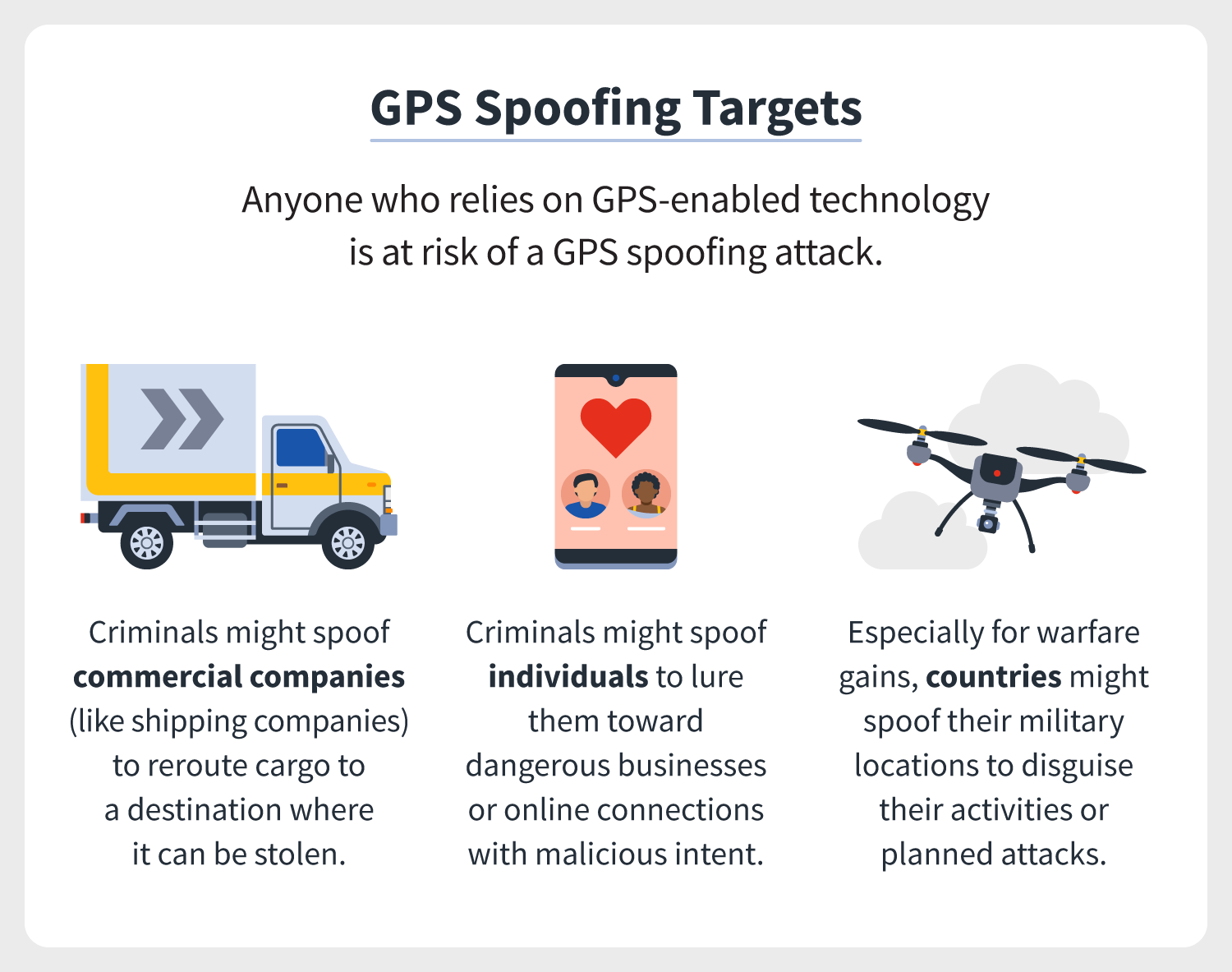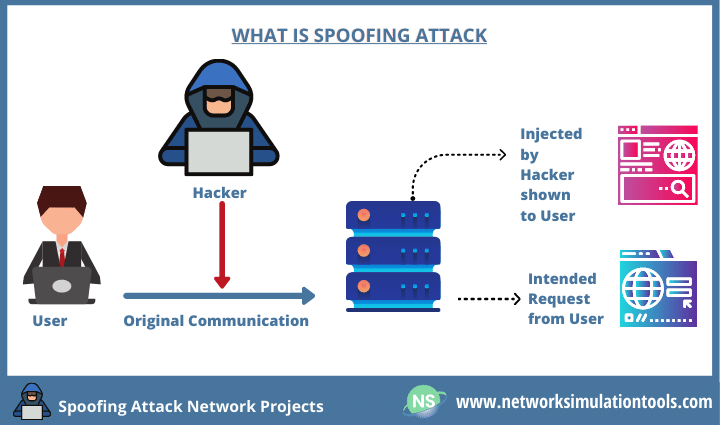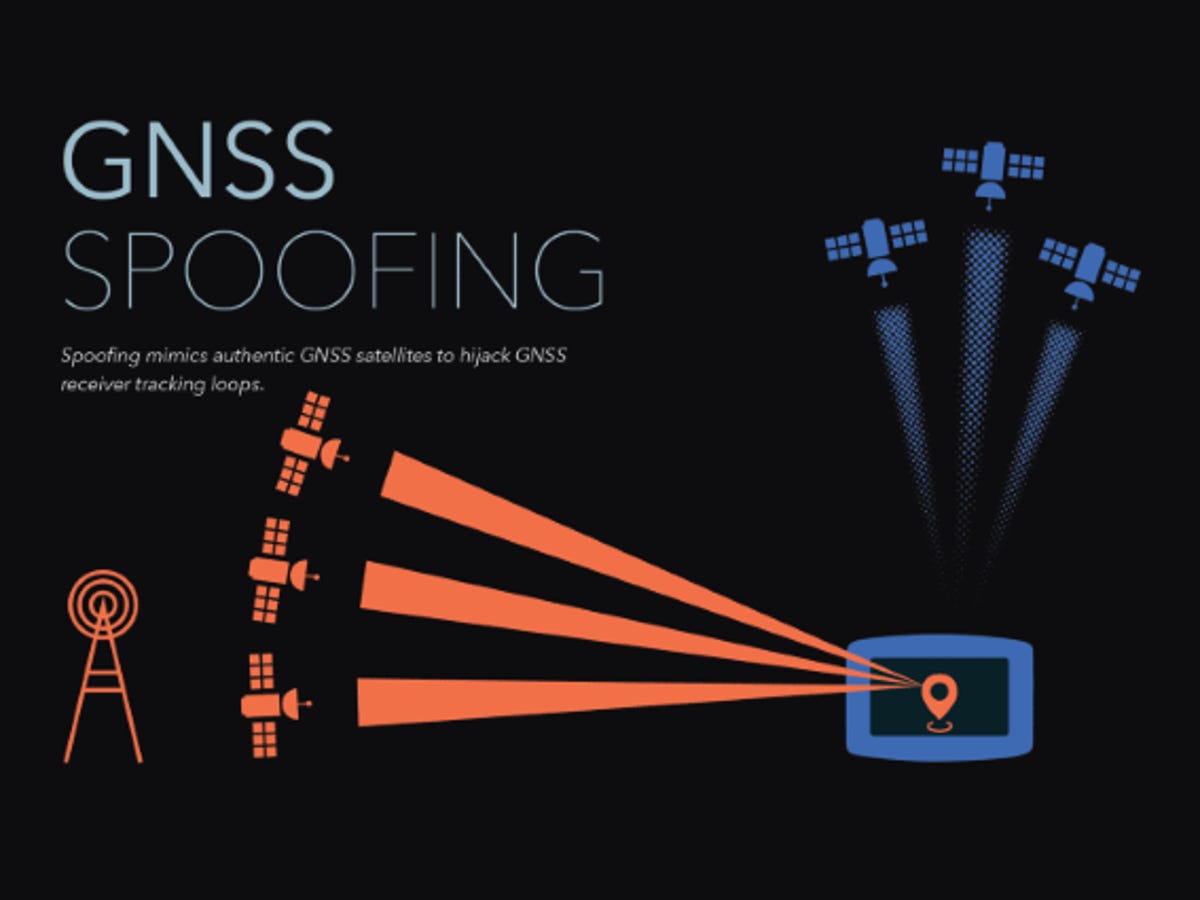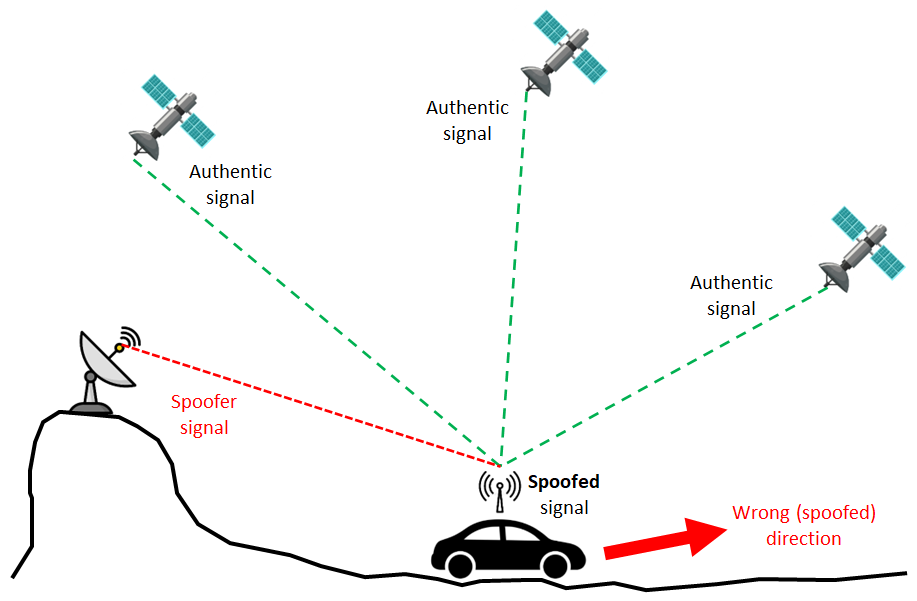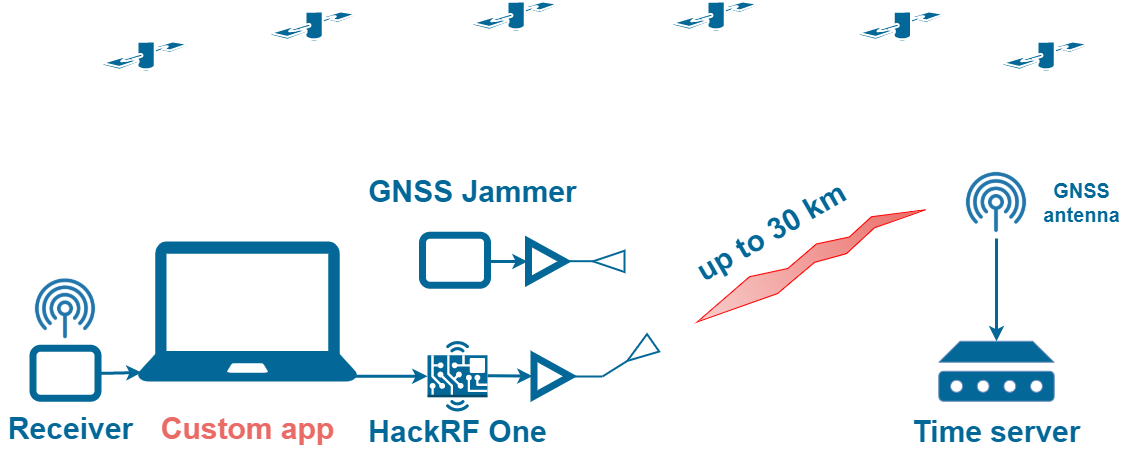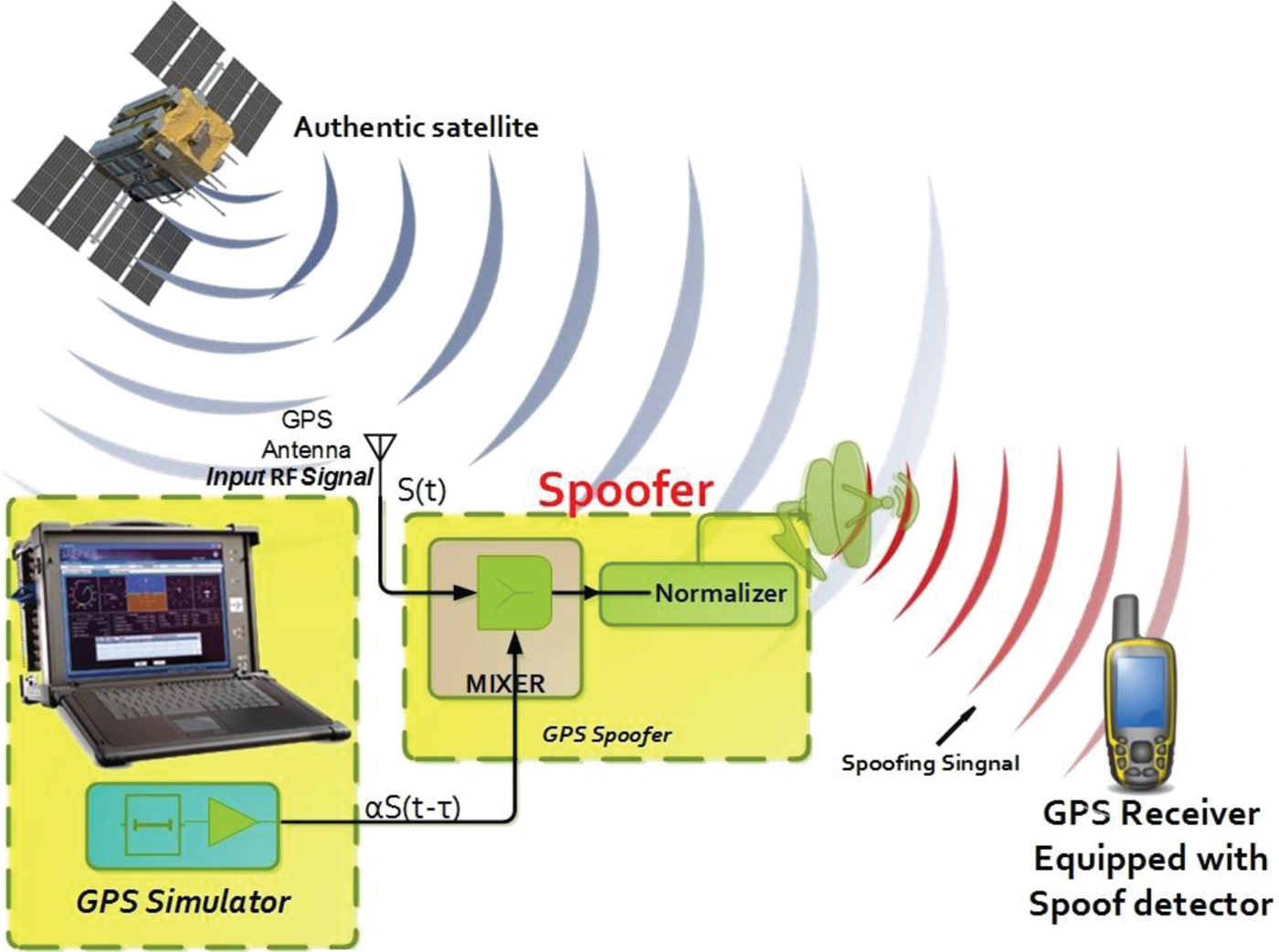
Detection of Spoofing Attack using Machine Learning based on Multi-Layer Neural Network in Single-Frequency GPS Receivers | The Journal of Navigation | Cambridge Core
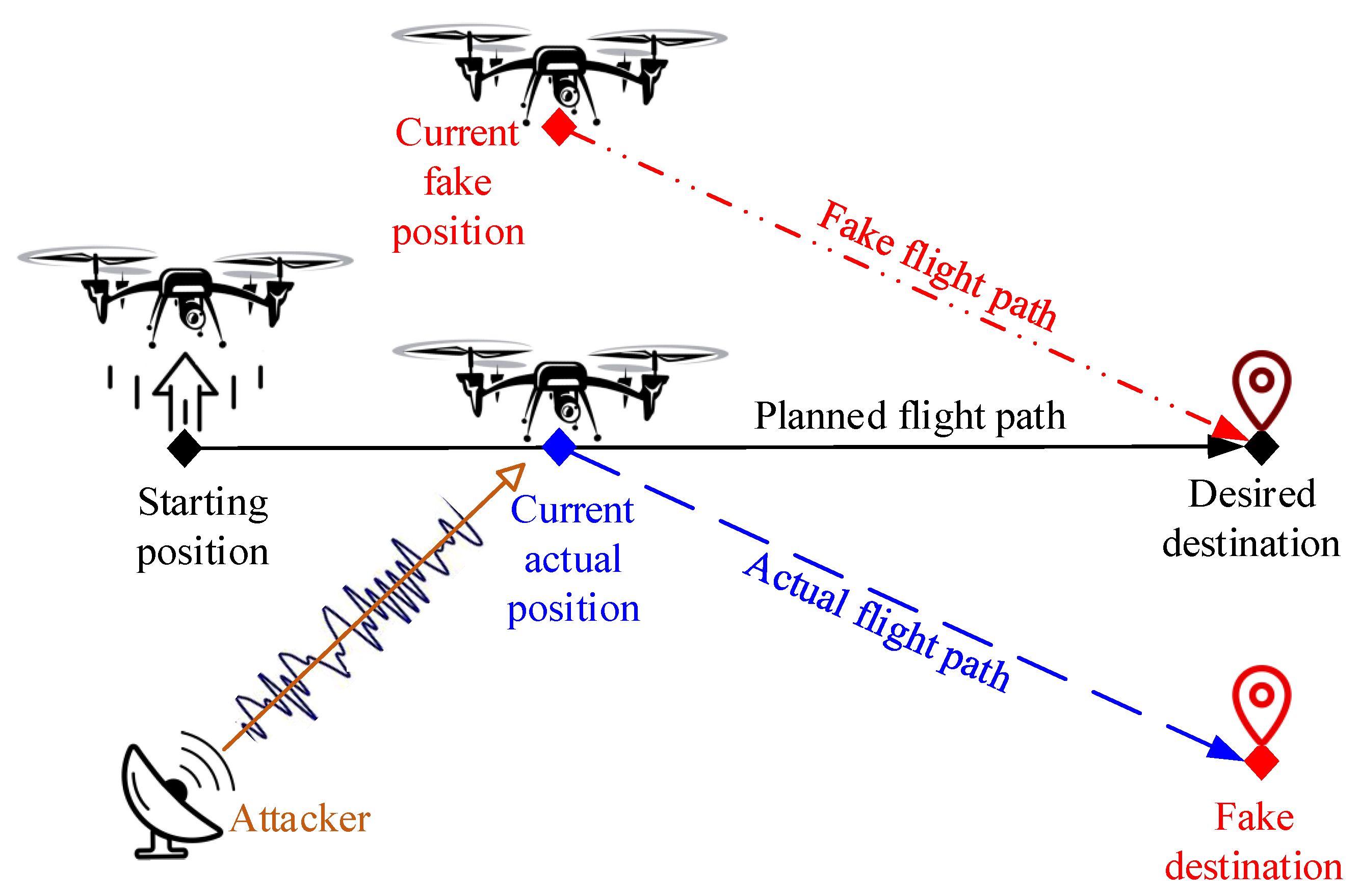
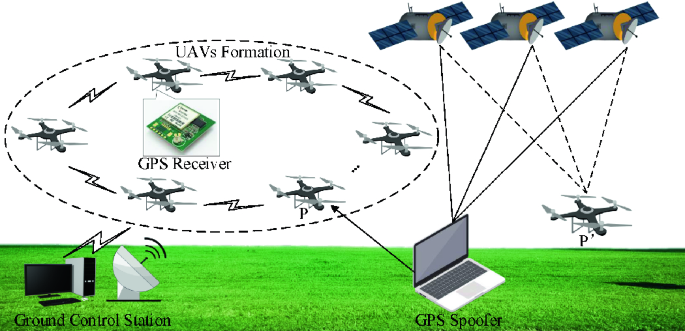
Remote Sensing | Free Full-Text | ConstDet: Control Semantics-Based Detection for GPS Spoofing Attacks on UAVs