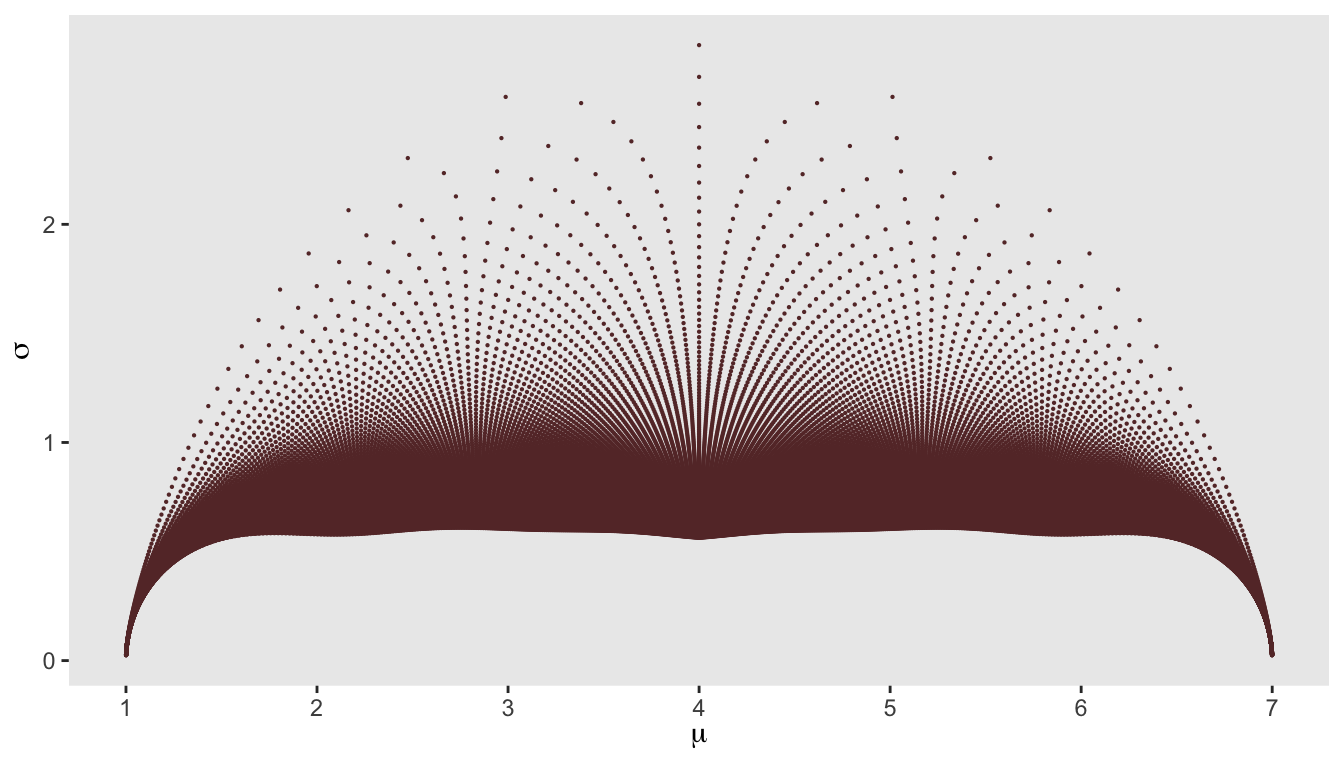
Data science for cybersecurity: A probabilistic time series model for detecting RDP inbound brute force attacks - Microsoft Security Blog

Brute force simulation accuracy vs. number of steps in the simulation.... | Download Scientific Diagram
Time taken for sub brute force attack Another simulation is conducted... | Download Scientific Diagram

e Procedure for the brute force technique in a two-step Monte Carlo... | Download Scientific Diagram

![PDF] Brute Force Attack of EPCglobal UHF Class-1 Generation-2 RFID Tag | Semantic Scholar PDF] Brute Force Attack of EPCglobal UHF Class-1 Generation-2 RFID Tag | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a7c683a4e52a04dabdceec4099f9353479b088aa/4-Figure2-1.png)
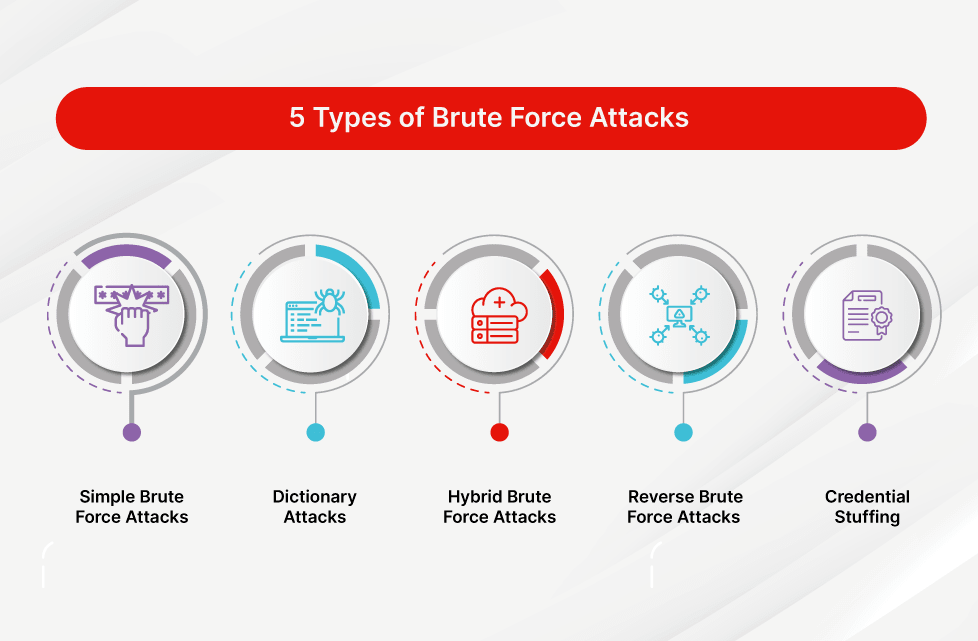

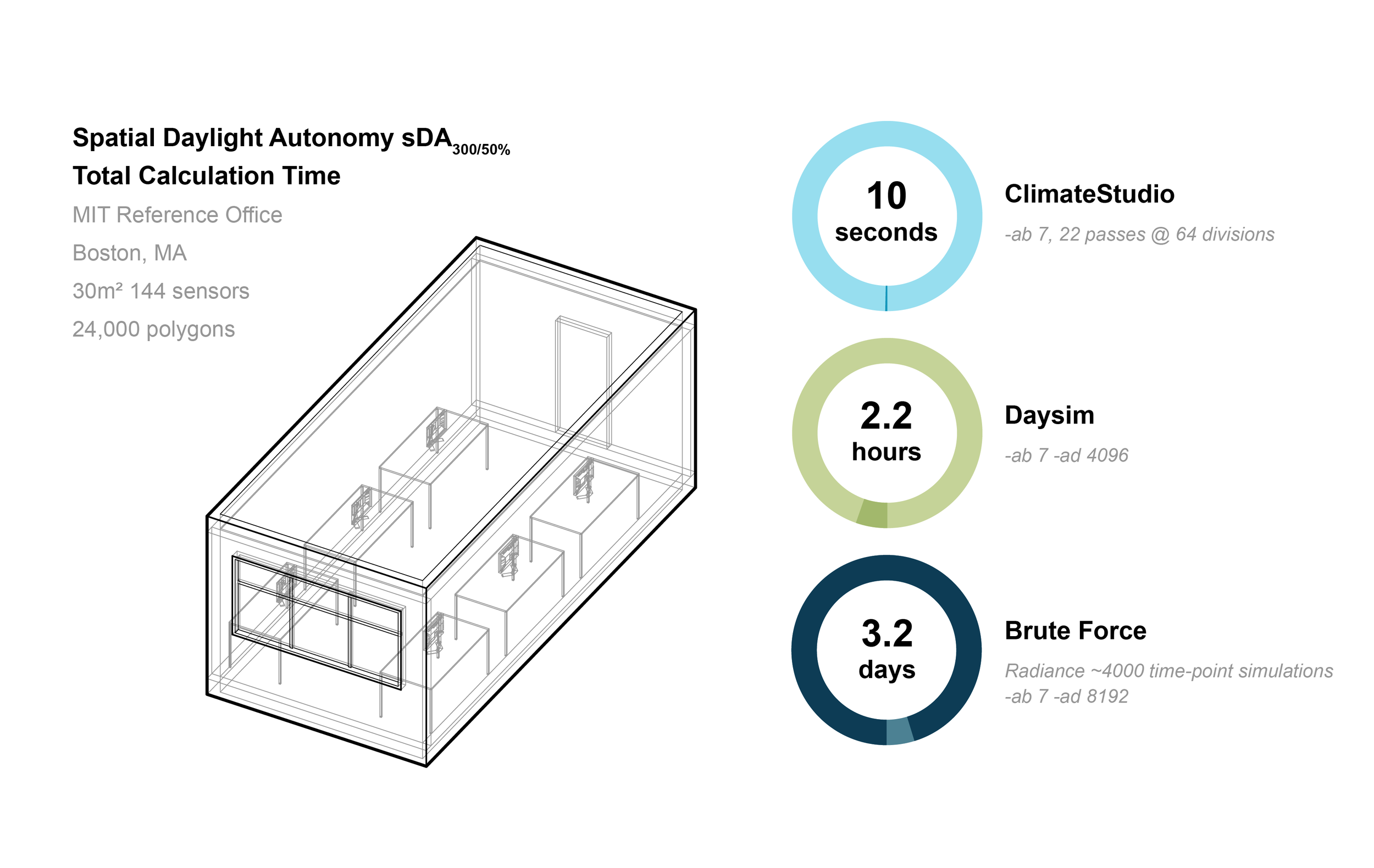

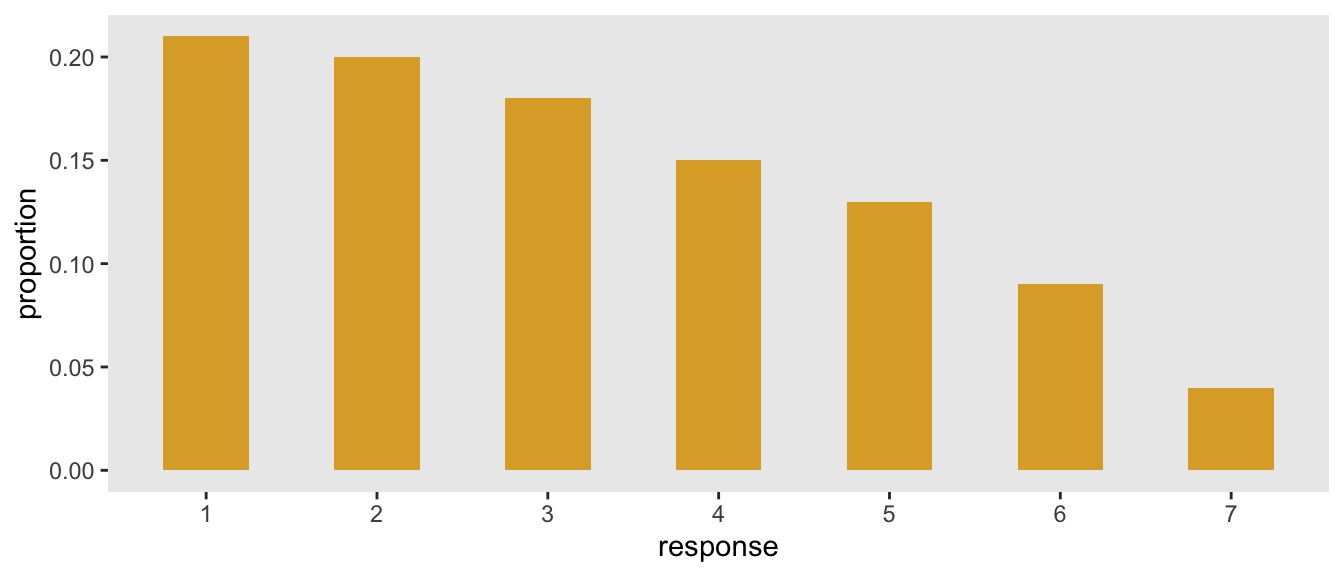

![Top 4 Cyber Attack Simulation Software [Network Security Tools] | Network Simulation Tools Top 4 Cyber Attack Simulation Software [Network Security Tools] | Network Simulation Tools](https://networksimulationtools.com/wp-content/uploads/2021/11/Top-4-Common-Cyber-attack-Simulation-Software.jpg)